Cybersecurity is all about information — not merely gathering data on malware and attacks but analyzing it and acting upon it. That’s what we call threat intelligence.
And action is not just reaction to something that’s already happened. It implies proactive measures of setting up detection systems, vulnerability management, and risk assessment.
In other words, threat intelligence is what helps organizations avoid the aftermath of hacker attacks. First of all — financial losses, reputation damage, operational disruption, and legal trouble.
Threat Intelligence in Practice
Let’s see how it actually works using just one solution: Threat Intelligence Lookup from ANY.RUN. TI Lookup is a professional search engine to navigate and study cyber threats, hackers’ tactics, techniques and procedures. It supports over 40 search parameters and a number of search operators to look for certain indicators of compromise (IOCs), of attack (IOAs), and of behavior (IOBs) that can alert about a possible or an ongoing attack.
Threat Intelligence Lookup can be of use to an organization’s Security operations center in most of the tasks it performs; we shall take three of the core ones for example.
Alert triage
Assessing and sorting notifications about possible threats is one of the main SOC’s challenges. It helps prioritize the signals of actual danger, allocate resources, and avoid alert fatigue, which analysts may suffer.
A simple example: say, your systems has detected a suspicious IP in the network traffic. How much attention should you pay to it? Just submit the IP in Lookup.
DestinationIP:”45.252.248.26″
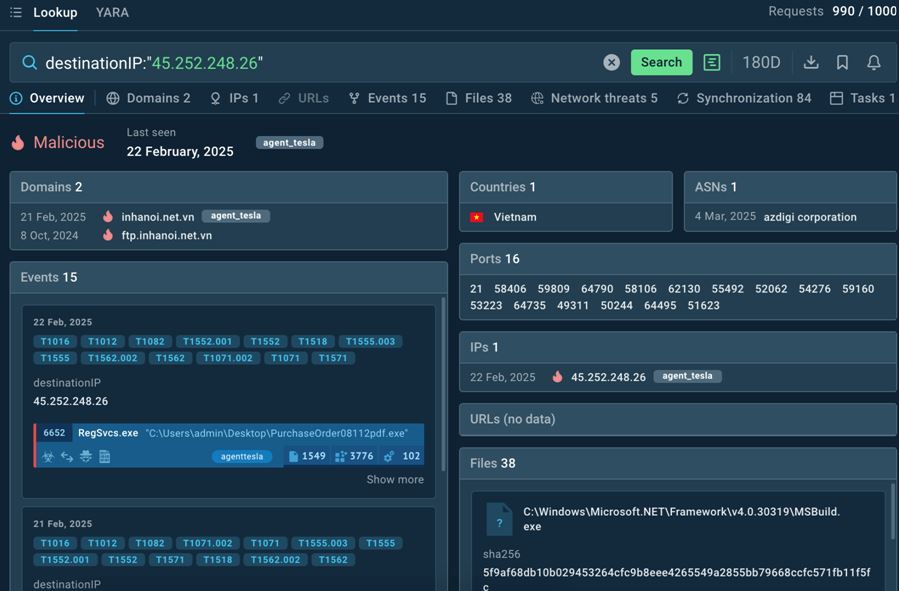
An IP search results that link it to known threat and give more IOCs
Here we are. The IP is labeled as malicious and tagged with “agent_tesla.” It’s part of the digital infrastructure of Agent Tesla, notorious keylogging spyware, and is associated with domains used in its attacks. If you see them inside your perimeter, it’s your priority to deal with it.
| See how TI Lookup can help level up your security operations Get 50 free search requests for trial |
Proactive Threat Detection
TI Lookup supports YARA rules: they are applied while scanning files, processes, or memory dumps for detecting characteristics and patterns specific for certain malware. The rules look like sets of instructions that describe what YARA should look for and under what conditions it should flag something as suspicious.
You can search TI Lookup using a pre-written rule or write your own. Suppose we have a rule spotting files used in Sakula (a remote access trojan) attacks.
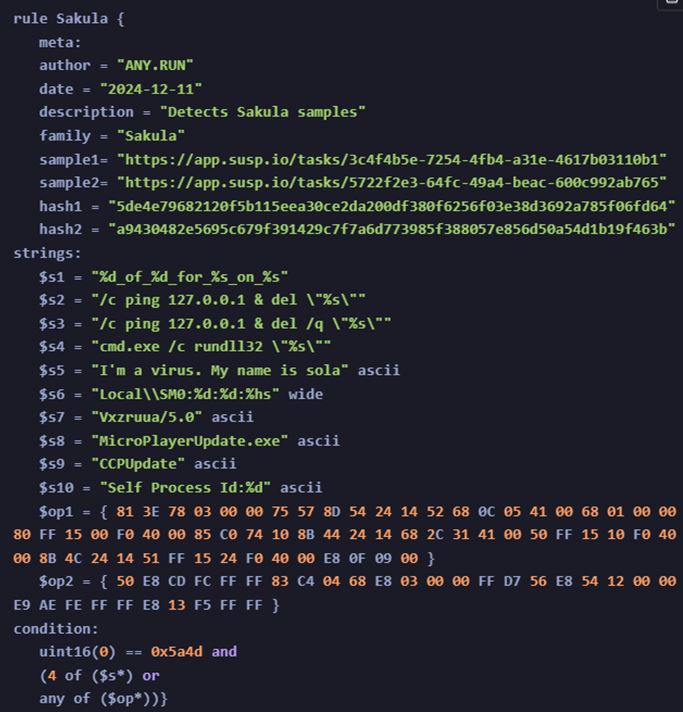
YARA rule for detecting Sakula malware
This rule’s search delivers a number of file hashes that can be indicators of upcoming incidents. What’s more, each hash is linked to a related task in the Interactive Sandbox, where samples of Sakula attacks are viewed and analyzed.
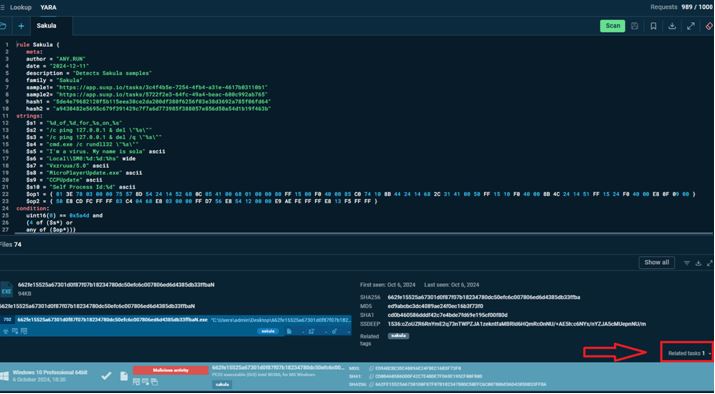
The results of Yara rule search
While exploring a sandbox analysis session found via a YARA rule search we can watch a malicious process edit Windows registry in the course of a Sakula attack.
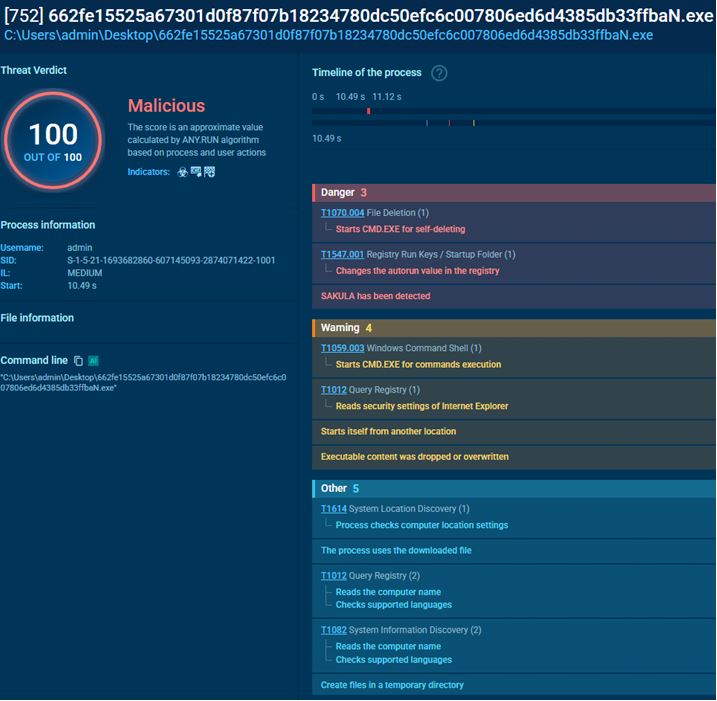
A malicious process that triggered a YARA rule
Incident Response
To respond to a cyber security incident means to limit or prevent damage from attacks or security breaches. The SOC team here intends to minimize injury to systems and data, reduce recovery time and cost, and control the harm to brand reputation.
In order to achieve all that, analysts must understand and predict the malware’s behavior and be sure that all malicious processes are detected and terminated. Additional indicators like mutexes can help to pinpoint an unfolding attack and add some clues about its operational mechanics. They also can be useful for further forensic analysis.
In TI Lookup, we can search for a definite indicator of attack and request additional indicators found in the same threat samples. Let’s search a malicious IP address with a parameter defining additional object type “mutex”:
destinationIP:”85.235.74.136″ AND syncObjectType:”mutex”
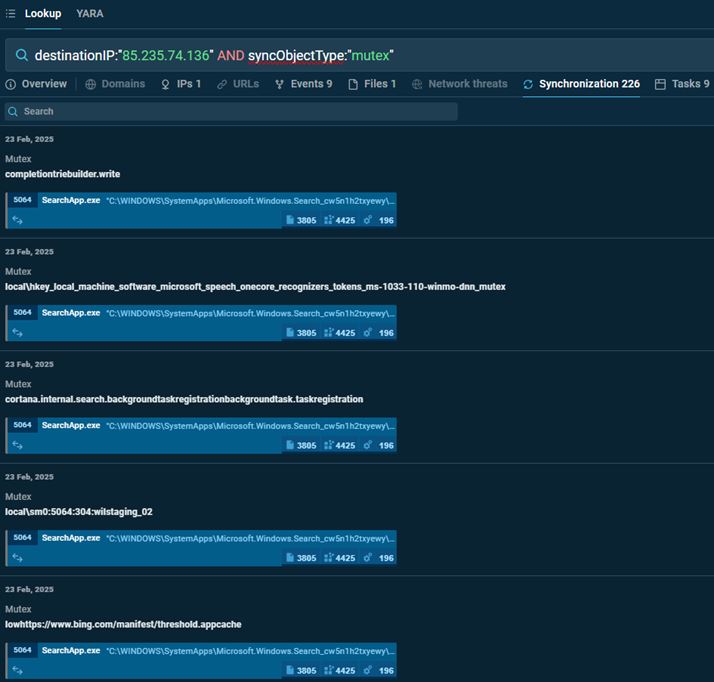
Mutexes associated with a malicious IP
The results complete our understanding of how Asyncrat trojan acts in the system.
Conclusion
By means of threat intelligence, you can not only gather basic and additional indicatios of compromise to set up your detection system but also understand and take under control an attack’s mechanics, triage alerts to give the critical ones priority, and compose your own threat detection rules to analyze network traffics and objects. Threat Intelligence Lookup can be of immense help with these tasks.










